I like Arch linux very much. Almost every piece of software I need can be found either in the official packages or in the Arch user repository. No need to search the Internet for a repo which contains 1 package you need right now.
There are rare situations though when its ‘rolling distro’ nature can bring inconveniences. But luckily it does not happen to often and solutions to overcome these inconveniences can actually help to discover some features of the software you didn’t know or require previously.
I had been using corporate VPN in my work daily. At some point, a standard VPN connection created in Gnome’s settings and managed by NetworkManager stopped working. It just could not start properly. After descent amount of time spent on troubleshooting, I decided to use a workaround - bring up the openvpn connection manually in a terminal and keep doing my usual stuff at work. It worked fairly well, but I still wanted to find a ‘fix’ to make the workflos more convenient.
Systemd Link to heading
The first brick of making the workflow smoother is to daemonize the process. It turned out to be rather simple.
There is a template file of openvpn-client@ service located in /usr/lib/systemd/system folder. let’s look at some of its parameters.
WorkingDirectory=/etc/openvpn/client
ExecStart=/usr/bin/openvpn --suppress-timestamps --nobind --config %i.conf
So if I put my .ovpn profile to a system-wide folder mentioned above, I should be able to start my VPN connection as a systemd service.
❯ sudo cp -v config.ovpn /etc/openvpn/client/my-vpn.conf
'config.ovpn' -> '/etc/openvpn/client/my-vpn.conf'
My connection profile assumes simple user/password authentication. There is automation for that also. I just put a file with my credentials (username and password on each line) near the connection profile and specified this directive in the profile.
auth-user-pass /etc/openvpn/client/.ncad
Let’s try to start the service.
sudo systemctl start openvpn-client@my-vpn
After a short time of initialization, the service should be up.
❯ sudo systemctl status openvpn-client@phxto
● [email protected] - OpenVPN tunnel for phxto
Loaded: loaded (/usr/lib/systemd/system/[email protected]; disabled; preset: disabled)
Active: active (running) since Sun 2024-11-10 15:15:15 EET; 28s ago
Invocation: e54649ba2e714804847331290fa94e63
Docs: man:openvpn(8)
https://openvpn.net/community-resources/reference-manual-for-openvpn-2-6/
https://community.openvpn.net/openvpn/wiki/HOWTO
Main PID: 154366 (openvpn)
Status: "Initialization Sequence Completed"
Tasks: 1 (limit: 18756)
Memory: 2.5M (peak: 7.2M)
CPU: 112ms
CGroup: /system.slice/system-openvpn\x2dclient.slice/[email protected]
└─154366 /usr/bin/openvpn --suppress-timestamps --nobind --config phxto.conf
So now I can invoke a memorizable command and give systemd the task of keeping my VPN connection alive and restarting it if needed.
Gnome extension Link to heading
But what if I wanted to see the indicator of my connection in Gnome’s top panel and possibly toggling it by one-two clicks? There are options of writing custom scripts or JavaScript plugins for Gnome, but for now I’ve found a simple Gnome extension called Systemd Manager.
It can be installed from AUR.
❯ yay -Ss gnome-shell-extension-systemd-manager
aur/gnome-shell-extension-systemd-manager 17-2 (+5 0.00) (Installed)
Gnome Shell extension to manage systemd services
Once installed, I only needed to add my openvpn-client@my-vpn service in settings and give it a display name.
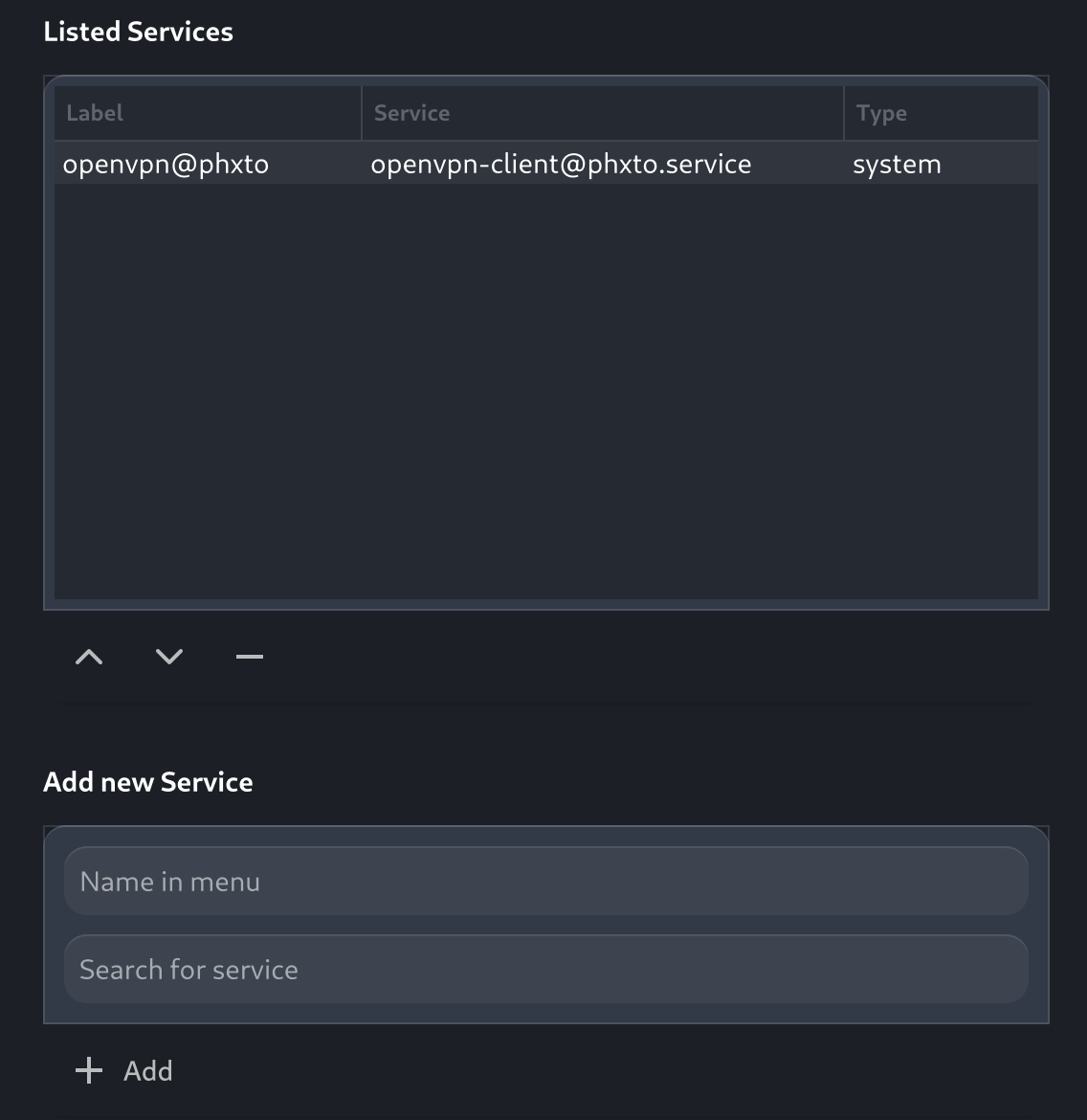
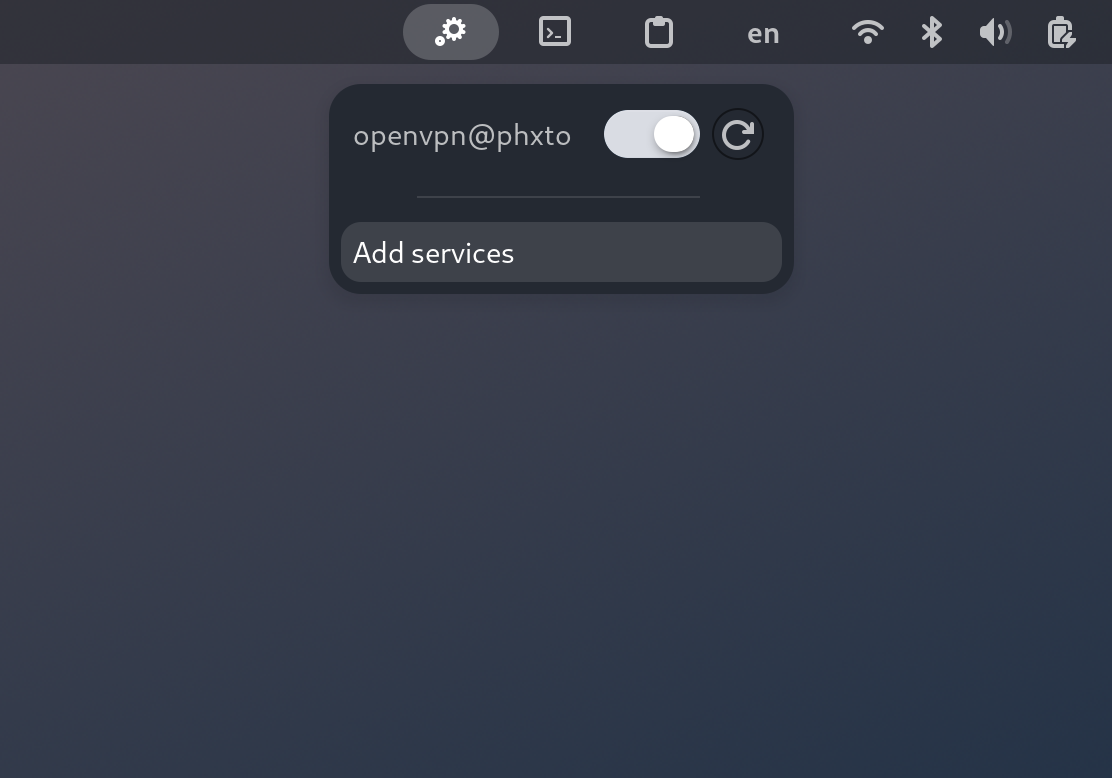
Now I have a toggle for my openvpn connection in my Gnome top panel!
Enforcing DNS settings Link to heading
One addiotional issue I was facing is that the DNS servers’ addresses from the VPN server were not added to /etc/resolv.conf automatically making a bunch of internal resources unavaible. To resolve this (pun unintended), I was able to find openvpn-update-resolv-conf-git package in AUR. There is also openvpn-update-systemd-resolved package for those who use systemd-resolved.
After installing it, I’ve added the following parameters to my connection profile which I had copied to /etc/openvpn/client/ earlier.
script-security 2
up /etc/openvpn/update-resolv-conf
down /etc/openvpn/update-resolv-conf
down-pre
Now the script is run every time the connection is brought up or shut down and the DNS settings pulled from VPN server are applied or reverted accordingly.